Brief Summary
Advent of EMR changes the life of patients, healthcare providers, and clerical staff. Modifying the entire healthcare working system, making it more efficient and productive. Moreover, it augments service quality score and care efficiency. However, data security is a significant concern in this cyber world. For this, doctors buy EMR data security systems. Is that so? No, there is much more to learn. Let’s start off.
Introduction
Maintaining healthcare security should be the foremost priority for you. If you think, by just leveraging the EMR software and your job is done. Then, you are absolutely incorrect on this.
Now, we need to be more aware because cyber crimes are higher than theft and forgery in this era. Is there any method to secure a new EMR platform? Yes, there are certain principles, if they are followed correctly and persistently.
Then, there are less chances of cyber crimes, enhancing document security to another level. It increases your patients’ trust and their engagement level. Additionally, it minimizes data breaches, reduces operational downtime, and decreases the risks of regulatory fines.
Security Challenges You Will Find In Electronic Medical Record
Indubitably, electronic medical records come with a lot of gains and data security risks. Cyber attackers use diverse tactics to steal healthcare data. Moreover, Let’s study in depth, what are the EMR data security challenges :
High Risks of Cyber Attacks
For cyber attackers, the healthcare industry is their main target due to the volume of personal and financial details at once. Based on the check point research in 2022, more than 1130 attacks occurred on an average in a week.
Nowadays, these numbers are increasing at a faster rate. Mostly, they used ransomware in the healthcare sector. Other kind of attack include :
- Phishing
- SQL Injection
- Malware
- DDoS
- Spoofing
- Third-party attacks
The healthcare sector costs more than other industries, more than $10.10 million per breach. It is the major disruption in patient care.
Failure To Abide Mandatory Rules
One of the main obstacles in pursuing regulations in healthcare, at each practice you need to follow varied rules. Furthermore, healthcare providers are always in a hurry and they don’t have sufficient time for checking notifications again and again.
Creates a big challenge of healthcare, let’s look how :
- Enhances system downtime
- Intervene of legal authorities
- Disrupting administrative duties
- Recovering with high expenses
- Increases patient data risks
Weak Password Enhance Fraudulent Activities
Strong passwords are required while using the electronic medical record solution. Otherwise, it cracked easily. Moreover, it has severe impacts like imposing hefty penalties and affecting healthcare reputation. Through weak passwords, cyber attackers can :
- Easily know what their passwords are
- Ask for ransom amount, increases costs
- Takeover one’s account
- Streamline to fetch recorded financial details
- Affecting the clinical routine
Directly, it increases the financial risks and loss of revenue within minutes and increases customer trust issues in healthcare.
Excessive Permissions Create More Risks
When there is no restriction against accessibility of healthcare documents, there are strong chances of :
- Unauthorized accessibility that can manipulate the situation
- Easily cross over from confidential data to patient conversation
- Considered HIPAA breach, which increases significant costs
- Shows the hospital negligence, affecting reputation
- Violates patient safety regulations
The electronic medical record solution increases the chances of malicious attacks, enhances patients distress, and can highly misuse information.
Internal Threat of Leaking Information
Significant threat is caused mainly because of two reasons, when the staff has decisive intentions and negligence behaviour. Furthermore, mostly they are trapped in the phishing scams and might damage the encrypted information.
Some employees have intentions for stealing money, so they directly take over their financial information and can utilize patent records for malicious intentions, which may harm patient reputation.
What Are The Core Features of EMR Data Security?
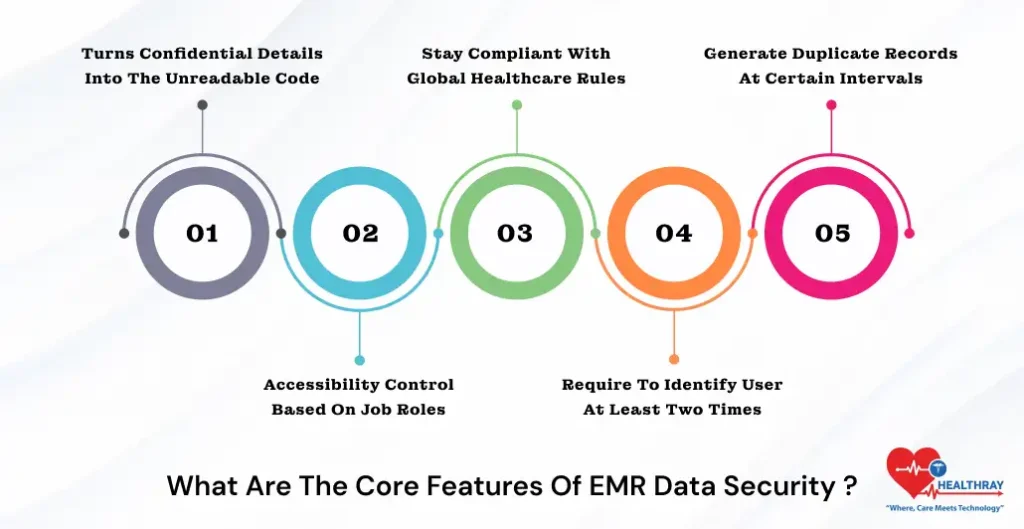
Imagine without EMR software, cannot be possible in this modern era because of their robust flexibility, budget-friendly system, and transparency. However, EMR data security system, more recommendable due to implementing robust security principles. Let’s talk about its core functions :
Turns Confidential Details Into The Unreadable Code
Convert sensitive healthcare information into code, this is the powerful method to prevent medical information against cyber attackers. It is called the encryption method, it does not only work when the information is stored but also works in case of transferring information.
- Strong algorithms have been used in diverse circumstances :
- Healthcare details saved in the cloud server – use AES-256
- Medical information transferring across systems and users – use TLS 1.3
- Asymmetric Encryption (RSA) for preventing management keys
In the large healthcare organization, they adopt homomorphic encryption, access control, and verification needed every time when you use it.
Accessibility Control Based On Job Roles
At this time, the management cannot build trust, if the case is related to the healthcare sector as the most sensitive one. Furthermore, traditional role based control is not a great choice in the modern era.
The EMR data security system categorizes the activities based on their expertise, assigning those documents which are relevant to their work. They have a restriction in the case of sharing extravagant information.
Stay Compliant With Global Healthcare Rules
EMR data security, in-built automation tools that only reminds you but the applying regulation without human intervention. Moreover, this single medical solution for all kinds of protocols whether its :
- HIPAA
- European Commission
- GDPR
- CMMI LEVEL 5
- AICPA SOC2
Require To Identify User At least two Times
This time is not for modifying the healthcare workflow service, making changes in the data security methods for more efficiency and increased patient satisfaction. Moreover, data accessibility travels to varied ways and locations in a care network. In that case, you can use these diverse strong methods to strengthen information and mitigates risks :
- Employed single sign-on (SSO) method
- Multi-factor or 2FA authentication
- Salting and hashing method
Among them, multi-factor is the easiest and strongest method, because it requires two or more time verification before log in.
Generate Duplicate Records At Certain Intervals
EMR data security automatically replicated copies of healthcare information at the predefined intervals. Moreover, you can set timing based on the need. Record medical documents in the cloud-architecture.
Therefore, registering details in the cloud server provides the availability from any location. Best approach for managing downtime and enhancing coordinated care. Therefore, it decreases workforce stress and enhances efficiency.
Step towards digital era with our healthcare solution
Revamp your hospital facilities and embrace change for better healthcare management. Ease in managing and organizing large medical datasets leads to effective analysis. Seize the opportunity now!
Why Do Doctors Prefer Security-enabled Electronic Medical Record Systems?
If the security principles are absent in the electronic medical record system, it would decrease its importance. Moreover, maintain coordinated care and help in improving patient safety. Here are other reasons:
Adverse Effects of Data Breaches
Serious impacts after breaching healthcare information, which does not affect a single patient but also creates a big obstacle in the longevity of hospitals. Let’s see what could be the adverse effects :
- Loss of revenue
- Reduces staff interest
- Legal interference
- Damaging reputation
Confidential Nature of Medical Data
The healthcare sector is a sensitive industry, its internal information should be protected. Otherwise, the patient data is at risk and its impact on hospital work. It encompasses :
- Medical details and treatment plans
- Financial Information
- Insurance and claim documents
- Legal papers of hospital
For Building Patient Trust
Patients are very conscious about their healthcare information, whether its medical images or financial information. Moreover, they want extreme privacy on their healthcare part. The data security in healthcare uses varied data and safeguarding principles that heightens power of efficiency and safety.
Medical documents cannot be transferred to any one without the prior approval of patients. Moreover, it increases the safety culture and in return, enhances trust among patients.
Reduces The Disruption Risks
Healthcare staff can work without any boundaries and stress. If the security algorithms are absent, it creates hindrances in work and mostly their time invested on listening to client inquiries. Furthermore, the secured EMR prevents the downtime in case of data loss or any cyber attack due to :
- Data recovery system
- Role based access control
- Smart access management
- Robust compliance
Enhance Clinic Reputation
Mainly, hospital reputation heavily depends on maintaining data secrecy and confidential patient-provider information. However, data breach has the potency to ruin it. To save from the reputation damage, adopting the Healthray EMR is the best choice.
Because it prevents 360 degree access, encrypted information, and secure collaboration with users and systems.
What Is The Future of Data Security In Healthcare?
Data security in healthcare, evolved persistently and created better ways to save information and minimizes extensive risks. Here are the future trends, may will occur in preventing information :
Anticipating Breaches With AI Tools
Leveraging the modern AI algorithms like deep and machine learning to comprehend the information pattern, what it said. Moreover, create a model that creates a great relationship with inputs and outputs.
Also, helps in predicting the accurate outcomes. If the website or any link occurs, it inspects the data risks and uses notification medium through conveying information.
Blockchain For Secure Transaction
There are high chances of using blockchain technology for managing financial transactions and records. It stores financial and patient information in the format of block chain and each of them is connected to each other.
It makes the transactional information immutable, data is not only available at the centralized level but also present in many computers. Patients use the cryptographic keys for substantial power over records.
More Dependable Upon Cloud-based System
A new way for preventing medical details, the cloud EMR will be the first choice of the healthcare institutions because it serves two purposes : First, save information in the remote server and second, maintain robust security in case of archiving or transit information.
Uses many methods to secure wide information such as threat inspection, audit control, enabling two factor authentication, and role-based access control (RBAS).
Conclusion
Maintaining data security renders peak level of coordinated care, reduces malicious attacks, increases patient safety, and heightens efficiency. Therefore, employing the EMR data security system is a must and growing security concerns make it more crucial. Having EMR is enough due to several bottlenecks, ranging from cyber attacks, weak password, internal threat, to excessive permission. The core functions of EMR data security include accessibility control, multi-factor authentication, and created data back ups. Maintaining data confidentiality, increases patient data trust, reduces disruption, and improves reputation. In the future, they might adopt AI algorithms, leverage blockchain, and the cloud-based system.